## Heads Up, CS2 Squads! Your Browser Could Be Your Downfall
Imagine this: you’re locked in a tense CS2 match, clutch rounds on the line, and suddenly, BAM! Your account gets hijacked. Before you can even yell “gg,” your hard-earned skins and rank are gone, leaving you with nothing but a bitter taste of defeat. This isn’t some Hollywood movie plot, folks. It’s the terrifying reality for some CS2 players thanks to a nasty new breed of cyberattack: browser-in-the-browser (BiTB) attacks.
Security researchers at BleepingComputer have uncovered a scheme targeting unsuspecting Steam users, and it’s all happening within the confines of your own browser.
We’re diving deep into this chilling threat, exploring how these attacks work and what you can do to protect yourself and your precious CS2 assets. Don’t let your browser becomeThe Navi Con: Weaponizing Fan Loyalty
The recent phishing campaign targeting Counter-Strike 2 players highlights a concerning trend in cyberattacks: the exploitation of fandom and brand recognition.
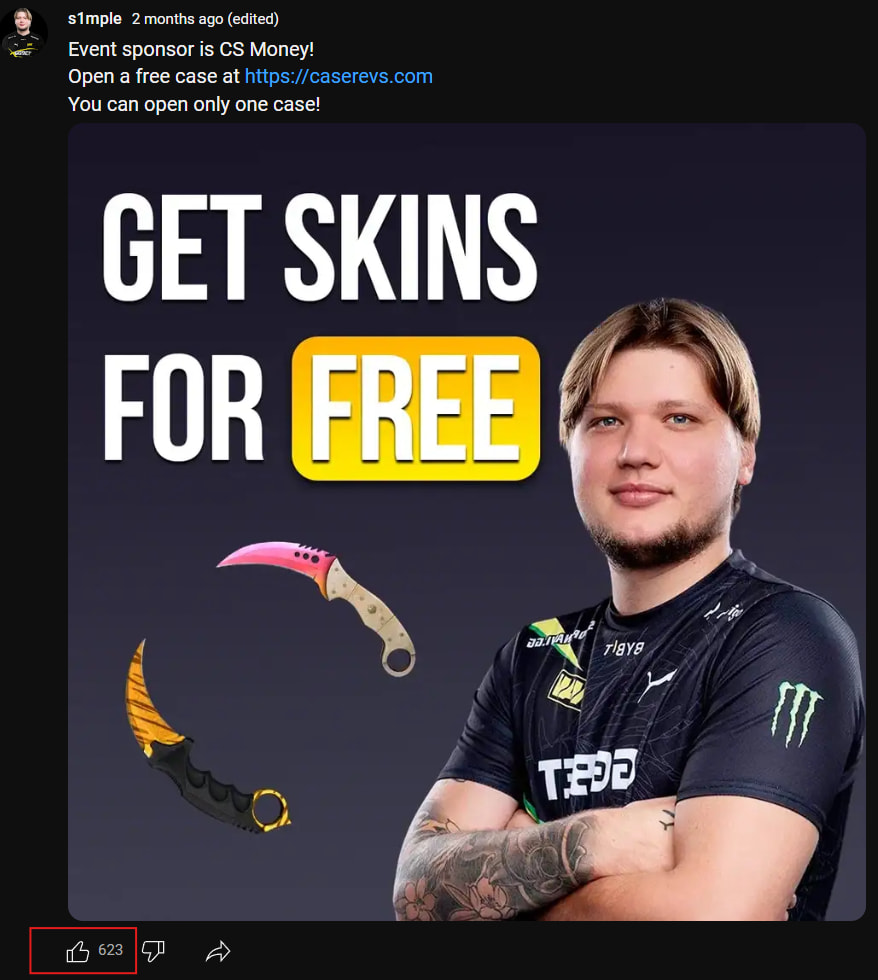
Gamestanza has learned that threat actors are leveraging the popularity of the renowned esports team Navi to legitimize their phishing attempts. Promising free CS2 loot cases and using Navi’s branding, attackers prey on the passionate fan base, hoping to trick them into revealing their Steam account credentials.
This tactic is particularly insidious because it preys on the trust and loyalty fans have for their favorite teams. Gamers, eager to secure in-game rewards, may be less vigilant when confronted with a seemingly official offer bearing a familiar brand.
The use of the Navi name and logo adds a layer of authenticity to the phishing websites, making them appear more legitimate and trustworthy to unsuspecting victims. This is a concerning development, as it demonstrates the lengths to which cybercriminals will go to exploit human psychology and manipulate users into compromising their security.
Spotting the Signs: Deciphering the Browser-in-the-Browser Deception
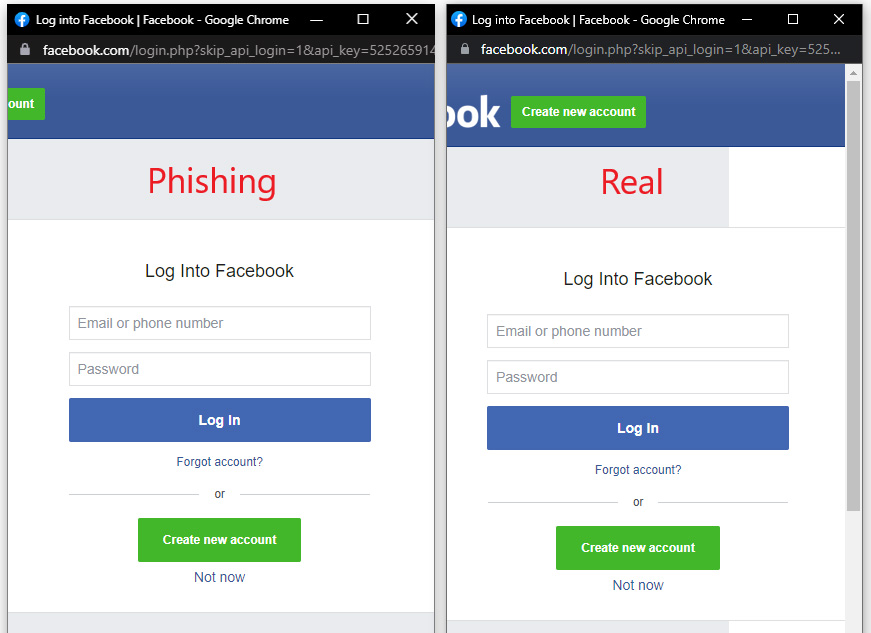
Understanding how Browser-in-the-Browser (BitB) attacks function is crucial for safeguarding your Steam account. Unlike traditional phishing attempts that redirect users to cloned websites, BitB attacks create fake browser windows within the user’s existing browser window.
These fake windows closely mimic the appearance of legitimate websites, making it difficult for users to distinguish them from the real deal. The attackers can even manipulate the URL and SSL certificate padlock to further deceive victims.

Key Indicators of a BitB Attack
- Unusual Window Behavior: Pay close attention to how the window behaves. Can you drag it outside the main browser window? Can you resize it? If the answer is no, it might be a BitB attack.
- URL Discrepancies: While the URL displayed in the fake window may appear legitimate, double-check it carefully. Hover your mouse over the link to see the actual URL. Even a minor difference could indicate a phishing attempt.
- Generic Design Elements: Be wary of generic design elements or inconsistencies in the website’s layout. Phishing sites often lack the same level of detail and polish as legitimate websites.
- Unexpected Popups: Be cautious of unexpected popups appearing within websites. Legitimate websites rarely use popups to request sensitive information like login credentials.
- Educate Yourself and Others: Stay updated on the latest phishing techniques and share this knowledge with your fellow gamers.
- Report Suspicious Activity: If you encounter a potential phishing attempt, report it to Steam and relevant cybersecurity authorities.
- Verify Information: Always verify information from unknown sources before clicking on links or sharing personal data.
- Be Skeptical of Offers: Be wary of unsolicited offers that seem too good to be true, especially those involving free in-game items or giveaways.

Steaming Up Your Security: Fortifying Your Steam Account
Protecting your Steam account from phishing attacks requires a multi-layered approach, encompassing both technical and behavioral safeguards.
Enabling Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring you to enter a unique code generated by an authenticator app or sent to your mobile device in addition to your password.
This significantly reduces the risk of your account being compromised even if your password is stolen.
Utilizing Steam Guard Mobile Authenticator
Steam Guard Mobile Authenticator is a dedicated app that generates time-sensitive codes for login verification.
It’s highly recommended to enable this feature for enhanced security.
Regularly Reviewing Login Activity
Log in to your Steam account regularly and review the “Login History” section to check for any suspicious activity.
Look for unrecognized login locations or times when you didn’t access your account.
Community Vigilance: A United Front Against Phishing
The gaming community plays a vital role in combating phishing attacks. By staying informed, sharing information, and reporting suspicious activity, gamers can create a safer online environment for everyone.
Conclusion
As gamers, we’re always on the lookout for the next big threat, but sometimes the danger lurks in the most unexpected places. This latest “browser-in-the-browser” attack targeting CS2 players on Steam serves as a chilling reminder that our digital security can be compromised even within the familiar confines of our favorite platforms. These attacks exploit vulnerabilities in seemingly harmless browser extensions, effectively hijacking user sessions and stealing valuable Steam account credentials. The implications are stark: accounts compromised, identities stolen, and precious playtime lost to malicious actors. This incident underscores the need for vigilance, urging every gamer to scrutinize the extensions they install and prioritize robust security practices. The future of gaming hinges on our collective awareness and proactive defense against these evolving threats. Remember, a lax approach to online security can cost you more than just a few game points; it can cost you your entire gaming experience.
